1. What is WPScan?
WPScan is a tool that is used to scan the WordPress website for Vulnerabilities. In this article, I am going to tell you. How to install and find Vulnerabilities in your WordPress site using WPScan.
WordPress is one of the platforms most commonly used for website development, currently, thousands of websites on the Internet use WordPress.
Using WordPress is a great advantage because it is free and practical, but we must be aware of the platform's security, because remember that it is an Open Source platform, where everyone has access to the source code, thus being able to exploit security flaws.
To keep your WordPress safe we recommend reading this article:
How to secure your WordPress website
Now let's move on to the more “fun” part, exploiting flaws and vulnerabilities in WordPress, so we will use the WPScan tool that is available by default on several Linux distributions for Pentest and can also be installed on Windows and other Linux distributions that are not targeted to perform intrusion testing.
The great strength of the tool alone is due to the fact that it lists themes, versions, plugins, subdomains, users, vulnerabilities, and application passwords in WordPress. It sounds like a joke, but thousands of sites are vulnerable.
To keep your WordPress safe we recommend reading this article:
How to secure your WordPress website
Now let's move on to the more “fun” part, exploiting flaws and vulnerabilities in WordPress, so we will use the WPScan tool that is available by default on several Linux distributions for Pentest and can also be installed on Windows and other Linux distributions that are not targeted to perform intrusion testing.
The great strength of the tool alone is due to the fact that it lists themes, versions, plugins, subdomains, users, vulnerabilities, and application passwords in WordPress. It sounds like a joke, but thousands of sites are vulnerable.
2. Installation of WPScan
So let's get started with WPScan Installation.
2.1 Installing WPScan on Ubuntu and Kali Linux
Open your Terminal and type the following commands:
sudo apt update (For updating Repositories)
sudo apt install curl git libcurl4-openssl-dev make zlib1g-dev gawk g++ gcc libreadline6-dev libssl-dev libyaml-dev libsqlite3-dev sqlite3 autoconf libgdbm-dev libncurses5-dev automake libtool bison pkg-config ruby ruby-bundler ruby-dev -y (This is for installing dependencies)
Now install WpScan using Ruby's gem installer
gem install wpscan
Hence the installation of WpScan in Ubuntu and Kali Linux gets completed.
2.2 Installing WpScan in Termux Android
Open your Termux app and type the following commands:
pkg install ruby
gem install wpscan
wpscan -h (for usage command)
Hence the installation of WPScan in Termux android is completed.
2.3 Installing WpScan in macOS
brew install ruby
gem install wpscan
Hence the installation of WPScan in macOS is completed.
2.4 Installing WpScan in Windows
Go to the official website of ruby by clicking below and download the Ruby installer for windows.
Now open your cmd and type the following command:
gem install wpscan
gem install wpscan
Done. Installation of WpScan on windows is completed.
3. Using WpScan Scanning a WordPress site for vulnerabilities
For this we will execute the command:
wpscan --url <YOUR WEBSITE HERE>
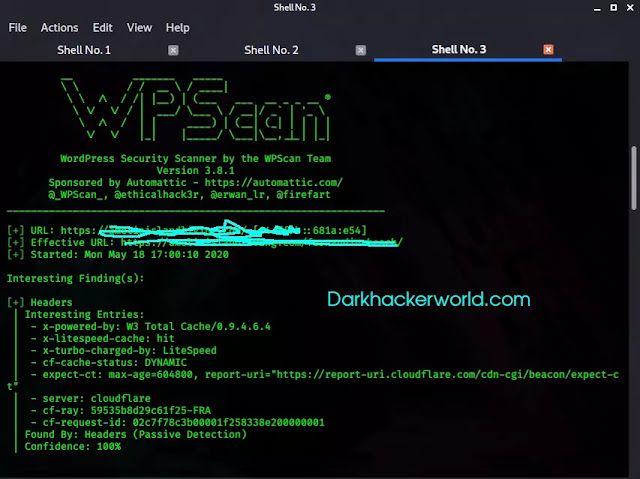
As we can see, we have found different items with potential vulnerabilities that could be used by an attacker to compromise our WordPress.
- XMLRPC.php (XML-RPC Interface) is open for exploitation like brute-forcing and DDoS pingbacks.
- Old WordPress version( may have a vulnerability in the current old Wordpress version).
- The external WP-Corn is enabled it would be possible to make a DDoS attack against wp-cron.php
- We also found a readme.html file. This file may contain some juicy information.
It is important to keep in mind that WPScan cannot determine the version of a specific plugin, it simply launches a list of potential vulnerabilities on the screen. Just because a plug-in version cannot be determined does not mean that the site is not vulnerable.
We must review the vulnerabilities that it details, visit the detail of the info that it shows us and run different exploits to know if our WordPress is vulnerable or not.
I link different URLs where we can find information relevant to potential vulnerabilities:
wpscan --url <YOUR WEBSITE> --enumerate u
After finding the users, create a wordlist, and type the following command or you can use any wordlist that is available.
wpscan --url <YOUR WEBSITE> --username admin --wordlist wordlist.txt
After running the above command successfully. The tool will attempt to crack the password for the admin user.
You can also use other functions of the tool, just read the documentation or type wpscan --help or just type wpscan to see the use of more parameters.
Secure your WordPress website
Thanks for reading our article. If you find our article helpful then feel free to comment below in the comment section.
4. Conclusion
In this article, we have learned how to install the WpScan in different types of Operating System and how to find vulnerabilities in the WordPress website with the help of WpScan. There are millions of website are present on the internet that runs on WordPress. And many of them are vulnerable. To secure your WordPress website you can read our article on how to secure your WordPress website by here:Secure your WordPress website
Thanks for reading our article. If you find our article helpful then feel free to comment below in the comment section.