12 Best Hacking Apps for Android In 2025
12 Best Hacking Apps for Android - Termux, Game Guardian, Kali NetHunter, ZANTI, Network Mapper, AndroRat, Netcut, Lucky Patcher and more.
12 Best Hacking Apps for Android -
1. Termux
2. Game Guardian
3. Kali NetHunter
4. ZANTI
5. Network Mapper
6. AndroRat
7. Netcut
8. Lucky Patcher
9. Cheat Engine
10. WIBR+ PRO
11. WPS Connect
12. Apk Editor
In today’s digital age, smartphones have become powerful tools for various tasks, including ethical hacking. Android devices, in particular, offer a wide range of applications that can help users understand and improve their network security. This guide will introduce you to the 12 best hacking apps for Android devices, focusing on their features, uses, and benefits. Whether you’re a cybersecurity enthusiast, a network administrator, or just curious about ethical hacking, this list will provide valuable insights.
Why Use Hacking Apps on Android?
Android devices are popular among ethical hackers due to their open-source nature and flexibility. These apps can help you perform tasks such as network analysis, penetration testing, and security assessments. They are useful for learning and practicing ethical hacking skills in a controlled environment.
Top 12 Android Apps for Ethical Hacking
Here is the list of 12 hacking apps on Android:
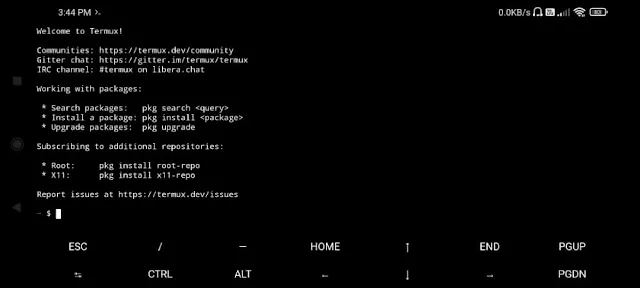
1. Termux
Termux is an app that brings the power of Linux to your Android phone or tablet. It lets you use all the tools and programs that Linux computers use. With Termux, you can run hacking tools like nmap, hydra, and sqlmap right on your Android device. It also lets you use the full set of Kali Linux hacking tools. Termux doesn't need special permissions or "root access" to work. It comes with a package manager that lets you easily install more Linux programs and tools. There are also extra apps you can get for Termux that help with hacking tasks like checking WiFi networks, taking apart computer programs, and more. Termux is very customizable, so you can set it up just how you like it. It supports coding languages like Python and Bash scripting. For people who do ethical hacking and cybersecurity work, Termux is a really useful tool because it brings Linux power to their Android devices.
Features of Termux
- Highly customizable
- Let's you experience the Linux shell on Android
- Comes with the APT package manager
- Best for ethical hackers and cybersecurity experts.
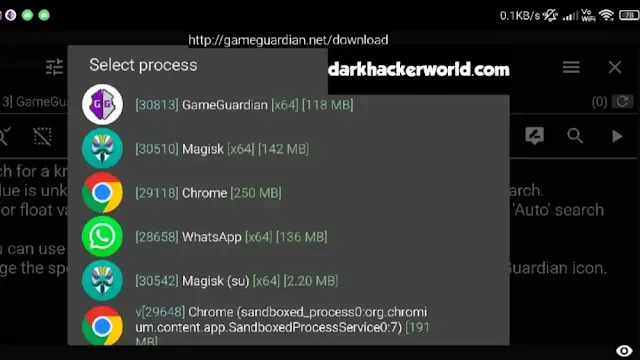
2. Game Guardian
Game Guardian is an app that helps you cheat in games on your Android phone or tablet. It can find and change secret numbers in a game's memory. These numbers control things like how much health, ammo, or game money you have. Game Guardian scans the phone's memory while a game is running. It looks for special patterns of numbers. You can then change those numbers to whatever you want. This lets you get unlimited health, bullets, coins, and more in games. It even works for online multiplayer games. However, to use all of Game Guardian's features, your Android device needs to be "rooted" - which gives you deeper access. Some people use Game Guardian just for fun cheating. But it can also help find and exploit security holes in games. Game Guardian supports many languages and can modify games as well as game emulators like PPSSPP. So in simple terms - it's a cheating tool that modifies a game's memory to give you an advantage!
Features of Game Guardian:
- Search encrypted values
- Dump and copy memory
- Search and modify values using third-party scripts such as .lua
- Available in more than 50 languages
- Support game emulators like PPSSPP, ePSXe, Game Boy, etc.
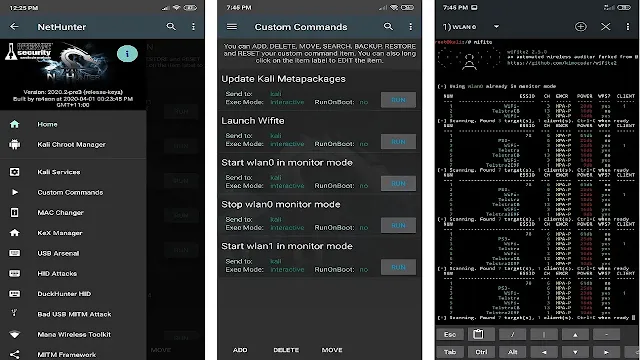
3. Kali NetHunter
Kali NetHunter turns your Android phone or tablet into a hacking machine! It has all the powerful hacking tools that hackers use on computer systems, but conveniently available on your mobile device. With NetHunter, you can hack into Wi-Fi networks, attack websites through the browser, spy on internet connections, and run lots of other hacking programs right from your Android. It comes loaded with famous hacking tools like Metasploit, Nmap, and Nessus that security experts use to test systems and find weaknesses. NetHunter lets you easily create and use special hacking programs called "payloads" on-the-go from your mobile. You can even customize NetHunter by adding your own hacking commands and functions to make it do exactly what you need. It has neat tricks like changing your device's Wi-Fi MAC address to become harder to track. Kali NetHunter packs a punch by bringing full hacking power to your Android for security testing and learning!
Features of Kali NetHunter:
- Perform all the ethical hacking tasks using an Android device
- It comes with a Metasploit Payload Generator that generates payload on the go
- It allows users to add their custom functions and commands to the launcher.
- Allows you to change your WiFi Mac address.
4. ZANTI (Zanti Android Network Toolkit Initiative)
Zanti is an app that lets you attack and hack Wi-Fi networks from your Android phone or tablet. But you shouldn't use it for bad purposes! With zANTI, you can see all the devices connected to a Wi-Fi network and keep an eye on them. It lets you hijack their internet sessions and spy on what they're doing online. zANTI can also redirect people's web browsers to trick sites that you control. This lets you send them viruses or steal their passwords when they log in. The app can even swap out images on someone's phone with other pictures you choose! To do these hacking attacks, zANTI uses clever tricks like ARP spoofing, DNS tricks, and removing security from websites. However, your Android needs to be "rooted" or have special access for zANTI to work properly. While zANTI has a simple interface, it's a powerful hacking tool. Good people can use it to test Wi-Fi security.
Features of zANTI:
- Browser redirection
- Session Hijacking
- Replace the image remotely on the phone
- Identify device properties
- SSL stripping.
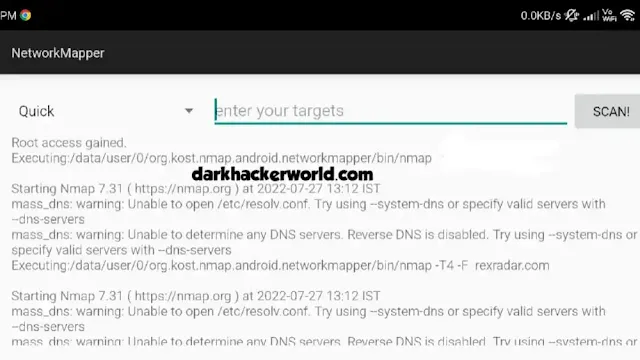
5. Network Mapper
The Nmap app lets you check and test computer networks from your Android phone or tablet. It's like a mobile version of a very popular network scanning tool used by professionals. With Nmap, you can search for all the computers, phones, and other devices connected to a network. It lets you see what "ports" or connections each device has open. Nmap can also try to guess what type of device and operating system something is running based on how it behaves on the network. It's really good at finding potential security holes and weak spots in networks and websites that hackers could exploit. The app supports all the same advanced scanning tricks as the regular Nmap tool that security experts use on computers. You can run Nmap scans over Wi-Fi or by connecting your Android directly to a network cable. It's very useful for computer network managers and security testers.
Features of Network Mapper:
- Scan web servers for vulnerabilities
- Firewall evasion
- Scan systems
- Scan for open ports, OS, and many more things
- Enumerating open ports of the target
- Host discovery.
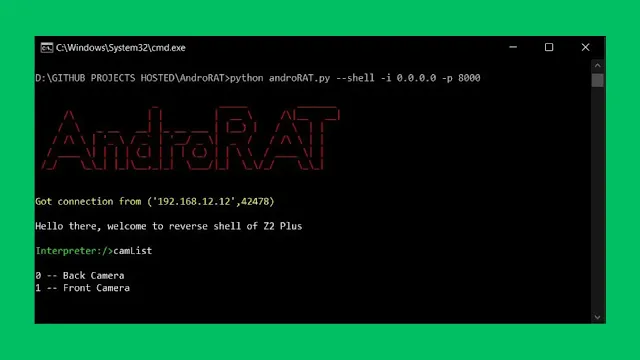
6. AndroRat
AndroRat is a hacking tool that can secretly take full control of someone's Android phone or tablet from far away. If AndroRat gets installed on an Android device, the hacker can basically do anything they want with that device remotely. They can see everything the victim user is doing on their device, like reading their messages, tracking their location, and even watching through the camera or listening through the microphone! The hacker can also make the victim's device do things, like vibrating, taking photos, sending texts, or even breaking the device so it doesn't work anymore. AndroRat is very sneaky and hard to detect because it hides itself on the device it has infected. Security professionals can use AndroRat for testing purposes.
Features of AndroRat:
- Check call logs using AndroRat
- Take photos remotely
- Send text messages without information to the victim
- Make the device vibrate
- View GPS location
Related Article - Best Termux tools for ethical hacking
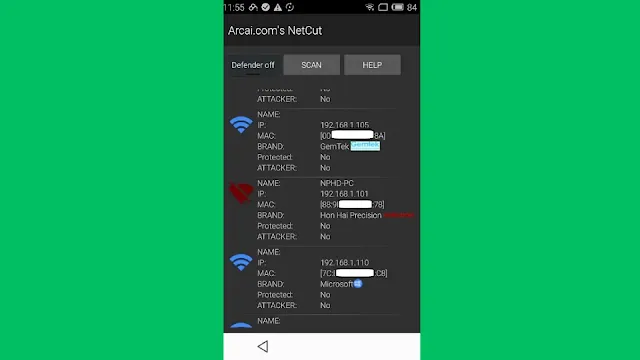
7. Netcut
NetCut is an app that lets you control which devices can use the internet on your Wi-Fi network at home. When you open NetCut, it shows you a list of all the phones, tablets, laptops, and other gadgets that are connected to your home Wi-Fi. The app lets you see how much internet bandwidth each device is using up. But the really cool part is that NetCut allows you to actually block devices from accessing the internet! So if your little brother is hogging all the internet for gaming, you can use NetCut to cut off his device's internet access with just a tap. NetCut does this by sending special coded messages to disconnect those devices from the Wi-Fi. NetCut can be a handy tool for parents or network admins to manage internet access.
Features of Netcut:
- Disconnect anyone from the Wi-Fi network
- Good user interface
- Find the MAC Addresses of All Connected Devices
- Control bandwidth usage.
8. Lucky Patcher
Lucky Patcher lets you change how other apps work on your Android device. But you have to be careful with it! With Lucky Patcher, you can remove annoying ads from apps, or bypass apps that want you to pay money to use certain features. It can basically trick paid apps into thinking you've already bought everything, so you get all the premium stuff for free! Lucky Patcher can also move apps from your phone's memory to an SD card to free up storage space. There's even a cool feature that lets you write your own code changes to totally modify how an app behaves.
Features of Lucky Patcher:
- Eliminate Licence verification of the apps
- Eliminate advertisements
- Store the apps on an SDcard
- Make in-app purchases free
- And many more features.
9. Cheat Engine
Cheat Engine is a special app that lets you cheat in video games on your Android phone or tablet! It works by looking inside the game's memory while it's running and finding secret numbers that control things like your score, health, money, and more. Once Cheat Engine finds those important numbers, it lets you change them to whatever you want! So you can give yourself unlimited lives, full health, infinite coins, and other cheat advantages. It can hack into all sorts of popular Android games like PUBG, Free Fire, and tons more. Cheat Engine has code-cracking tools to bypass the security of different game engines. But for Cheat Engine's full hacking powers to work, your Android device needs to be "rooted" which gives it deeper system access. You can even use Cheat Engine to create and share your own personal cheats and hacks for games! While really cool for gamers, Cheat Engine can also help security experts find vulnerabilities in games to improve their defenses.
Features of Cheat Engine:
- Modify video games
- Hack any Android game by modifying in-game binary values
- Can hack games like PUBG, Free Fire, and many more
- Create your cheats for the cheat engine
- Open-source tool.
Related Article - Android apps to learn to code
10. WIBR+ PRO
WIBR+ PRO helps you crack the passwords of Wi-Fi networks from your Android phone or tablet. It does this by secretly listening to when people connect their devices to a Wi-Fi network. During this "handshake", it captures a coded version of the Wi-Fi password. Then WIBR+ tries to figure out the real password by guessing loads of possibilities really quickly. It has huge lists of common passwords it can try. WIBR+ can use special hacking techniques like "Pyrit" and "coWPAtty" attacks to crack Wi-Fi passwords faster. The app can also check if a router is using its default password from the factory, which is easy to break into. Once it cracks a Wi-Fi password, you can then connect to that network from your Android! This app is very useful for security experts testing networks.
Features of WIBR+ PRO:
- Check your router is vulnerable to the default pin
- Easy brute force WPA/WPA2PSK Wi-Fi network
- Offline pin calculator
- Copy saved passwords
- Password recovery.
11. WPS Connect
WPS Connect is an app that can help you connect to WiFi networks, even if you don't know the password. It does this by guessing the special code (called a PIN) that is used to secure some WiFi networks. The app works by trying many different PIN codes until it finds the right one. When it gets the correct PIN, it can then access the WiFi network and connect your device.
Features of WPS Connect:
- Automatic configure SSID and WPA security key
- PIN method to connect with password-protected WPS-enabled Wi-Fi network
- Easy to use.
12. Apk Editor
APK Editor is a tool that lets you open and change Android apps. You can take apart an app, look at its code, and make changes. For example, you can modify images, text, and permissions inside the app. After making changes, you can rebuild the app into a new file. APK Editor is useful for developers who want to study how apps work or customize them.
Features of APK Editor:
- Edit and modify Android apps
- Create modified Android games and apps
- Remove unwanted permissions
- Change the logo and images of the app
- And many more features.
Related Article - 10 Best programming languages for Hacking
Conclusion
The post talked about 12 different hacking apps on Android. These apps are very powerful tools for good cybersecurity experts to test and fix problems with phones. As phones get more advanced, the hacking tools also get better. So we have to keep working hard to keep phones safe and secure from those who might want to misuse these powerful hacking apps.


Post a Comment